Let's study the Blockchain architecture by understanding its various components:
What is a Block?
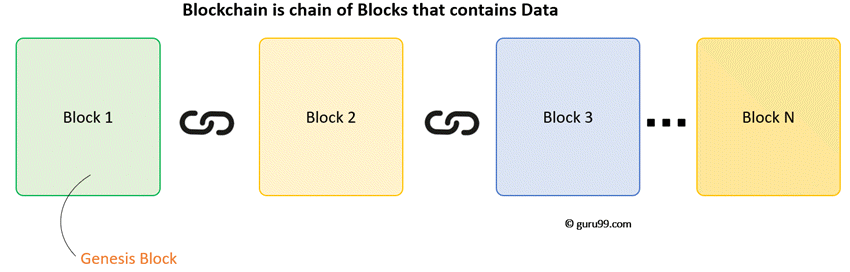
A Blockchain is a chain of blocks which contain information. The data which is stored inside a block depends on the type of blockchain.
For Example, A Bitcoin Block contains information about the Sender, Receiver, number of bitcoins to be transferred.
The first block in the chain is called the Genesis block. Each new block in the chain is linked to the previous block.
Understanding SHA256 - Hash
A block also has a hash. A can be understood as a fingerprint which is unique to each block. It identifies a block and all of its contents, and it's always unique, just like a fingerprint. So once a block is created, any change inside the block will cause the hash to change.
Therefore, the hash is very useful when you want to detect changes to intersections. If the fingerprint of a block changes, it does not remain the same block.
Each Block has
- Data
- Hash
- Hash of the previous block
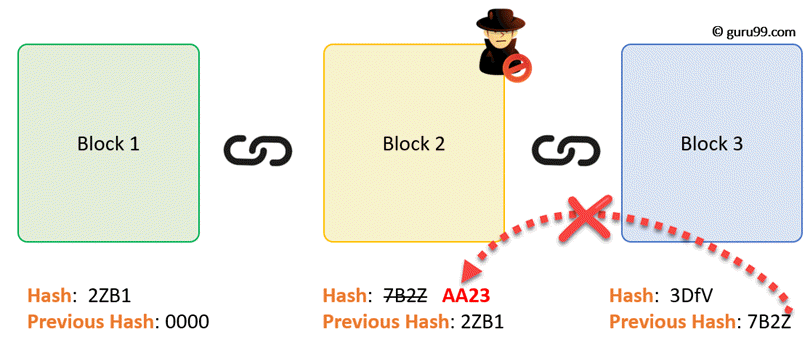
Consider following example, where we have a chain of 3 blocks. The 1st block has no predecessor. Hence, it does not contain has the previous block. Block 2 contains a hash of block 1. While block 3 contains Hash of block 2.
Hence, all blocks are containing hashes of previous blocks. This is the technique that makes a blockchain so secure. Let's see how it works -
Assume an attacker is able to change the data present in the Block 2. Correspondingly, the Hash of the Block also changes. But, Block 3 still contains the old Hash of the Block 2. This makes Block 3, and all succeeding blocks invalid as they do not have correct hash the previous block.
Therefore, changing a single block can quickly make all following blocks invalid.
Proof of Work
Hashes are an excellent mechanism to prevent tempering but computers these days are high-speed and can calculate hundreds of thousands of hashes per second. In a matter of few minutes, an attacker can tamper with a block, and then recalculate all the hashes of other blocks to make the blockchain valid again.
To avoid the issue, blockchains use the concept of Proof-of-Work. It is a mechanism which slows down the creation of the new blocks.
A proof-of-work is a computational problem that takes certain to effort to solve. But the time required to verify the results of the computational problem is very less compared to the effort it takes to solve the computational problem itself.
In case of Bitcoin, it takes almost 10 minutes to calculate the required proof-of-work to add a new block to the chain. Considering our example, if a hacker would to change data in Block 2, he would need to perform proof of work (which would take 10 minutes) and only then make changes in Block 3 and all the succeeding blocks.
This kind of mechanism makes it quite tough to tamper with the blocks so even if you tamper with even a single block, you will need to recalculate the proof-of-work for all the following blocks. Thus, hashing and proof-of-work mechanism make a blockchain secure.
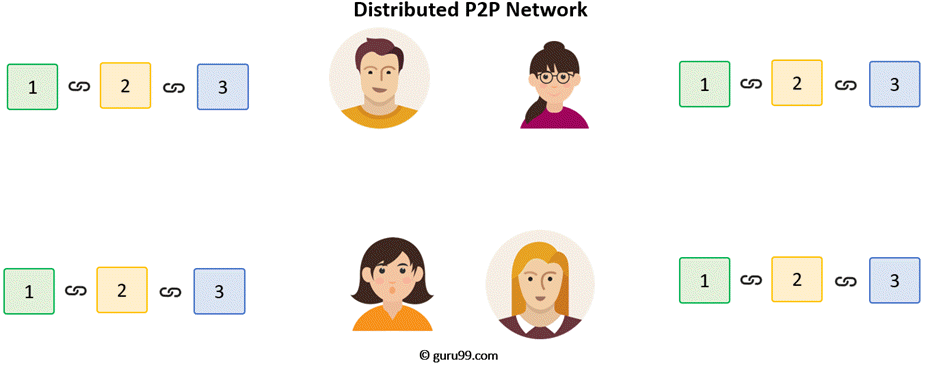
Distributed P2P Network
However, there is one more method which is used by blockchains to secure themselves, and that's by being distributed. Instead of using a central entity to manage the chain, Blockchains use a distributed peer-peer network, and everyone is allowed to join. When someone enters this network, he will get the full copy of the blockchain. Each computer is called a node.
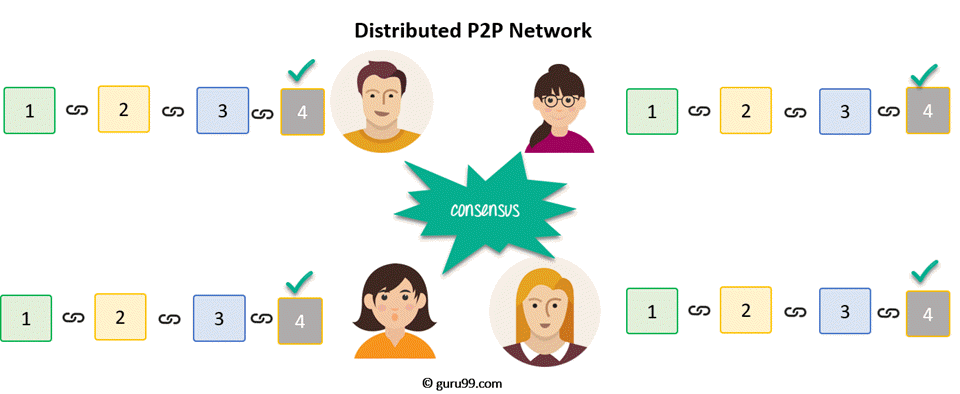
Let's see what happens when any user creates a new block. This new block is sent to all the users on the network. Each node needs to verify the block to make sure that it hasn't been altered. After complete checking, each node adds this block to their blockchain.
All these nodes in this network create a consensus. They agree about what blocks are valid and which are not. Nodes in the network will reject blocks that are tampered with.
So, to successfully tamper with a blockchain
- You will need to tamper with all blocks on the chain
- Redo the proof-of-work for each block
- Take control of greater than 50% of the peer-to-peer network.
After doing all these, your tampered block become accepted by everyone else. This is next to impossible task. Hence, Blockchains are so secure.




No comments:
Post a Comment